What's a vulnerability assessment? And how it works?
A vulnerability assessment is an essential starting step to surveying your association's receptiveness to security challenges, including physical and computerized security.
It can likewise be portrayed as a lot of specific tests planned to recognize deficiencies in your network and its key programming and equipment frameworks. It reveals inadequacies that hackers and unapproved clients can leverage on, inciting network failure and data burglary.
It tends to be executed by outside IT staff or by one inside the organization that focuses on doing weakness appraisals.

Various types of vulnerability assessment
- Host Assessment
It alludes to the assessment of significant servers, which may be presented to misuse if not inspected as expected or not made through a tried machine picture. Network and wireless evaluation – the assessment of practices and methods to keep away from undesirable admittance to private or general networks, and resources that are accessible to network
- Database Assessment
Enormous data and data set assessment systems for weaknesses and misconfigurations, recognizing maverick data sets or uncertain dev. /test conditions, and arranging sensitive data across a company’s structure.
- Application outputs
This alludes to the identification of safety shortcomings in the source code of web applications and the web applications through automated outputs toward the frontend or static/dynamic assessment of source code.

A few Options to Keep Weaknesses from Being Exploited – Guide
- Vulnerability Assessments should be done routinely, and the results detailed in an action log
If by chance that you discover that weakness is spotted, you have various choices to keep them from being exploited:
- Use Compensating Controls
Compensating controls can be viewed as instruments and approaches that you complete to get systems from assaults. Compensating controls invigorate the security of the structure or the overall security climate. Be that as it may, they don't absolutely clear out the danger to the system.
For example, if a weakness is seen in a firewall, you can complete IDS before the firewall to evaluate for assaults.
- Make a fix the board program
Another method to guarantee your system is secured is to make and complete a patch management program. As discussed, programming shortcomings are recorded consistently.
Merchants quickly release patches to address the shortcomings. Notwithstanding, users don't use their systems. This is in light of the fact that they don't have even the remotest clue about the presence of the weaknesses, or they don't know how to apply the patches. To fix this, you should make and execute a patch management program.
A patch management consolidates two segments: a cycle to discover and recognize shortcomings, and a system for applying the patches.
- Apply a weakness management program to perceive and zero in on the weaknesses that you need to fix
Consistent appraisals of your networks and systems should be done reliably, and the results recorded in an activity log.
The delayed consequences of these appraisals should be assessed by a panel of ranking staff. The board should sort out which weaknesses require brief thought and which ones can be tended to later. Right when a weakness is spotted, you should zero in on the weakness relying upon the degree of risk it presents.
The danger assessment brings up the likely impact of the weakness. At whatever point the circumstance permits, you should similarly recognize the threat. This is used to recognize the likelihood that the danger will exploit the weakness.
- Perform host and network solidification
Host and network solidification is a method of making your system safer by changing the security settings on it. The security settings on your system can be changed by designing the applications and working system, or by using security devices, for instance, firewalls and interruption discovery system(IDSs).
Perhaps the best ways to deal with set your system is to weaken pointless services. This is a direct strategy to diminish the assault surface of your framework.
Another way to solidify your system is to weaken unnecessary ports. This should be done on your routers, workstations, and servers.
For example, if you don't need to use the File Transfer Protocol (FTP) on any of your system, you should eliminate it. In case you don't need to use the Simple Network Management Protocol (SNMP) on any of your systems, you should eliminate it also. You can moreover plan firewalls to limit induction to certain ports.
- Perform weakness appraisals reliably to perceive new shortcomings
These appraisals similarly give a comprehension of new assault vectors that are yet to be known and can be used to make new arrangements to get against these weaknesses.
Be certain that no realized weaknesses are on your network. If any weaknesses are spotted during a danger assessment, address them immediately.
Apply the norm of least benefit. Limit permission to resources just to the people who need it to take care of their work. Show workers the necessity of guaranteeing office data.
To find more about safeguarding your association from advanced assaults, go to the National Cyber security and Communications Integration Center (NCCIC) site.
- Carry out a security mindfulness program
Instruct workers on security dangers and shortcomings. A security mindfulness program is used to teach users about the perils they face and the safety measures they should take to protect themselves. A security mindfulness program should consolidate correspondence strategies and teach techniques to build mindfulness
Weakness evaluation devices
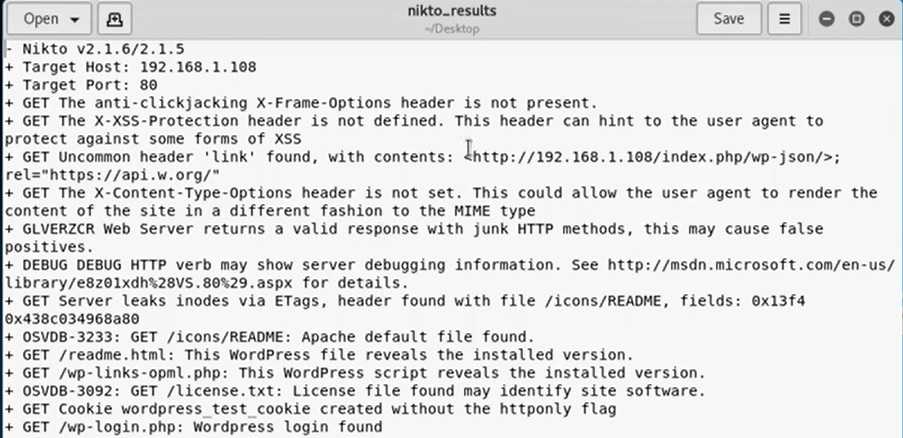
- Nikto2
This is an open-source weakness inspecting program that bases on the security of web applications. Nikto2 can find around 6700 unsafe records causing difficulties to web servers and report outdated servers based versions. Furthermore, the device can alert on server arrangement issues and perform web server filters within a brief timeframe.
Nikto2 doesn't give any countermeasures to shortcomings found nor give hazard evaluation functionalities. Regardless, Nikto2 is a frequently updated tool that enables a more broad consideration of weaknesses.
- Netsparker
Netsparker is another web application weakness instrument with a computerization feature utilized for finding weaknesses. This instrument is additionally prepared for finding weaknesses in a few web applications two or three hours.
Regardless of the way that it is a paid venture level vulnerability instrument, it has numerous premium features. It has crawling innovation that finds weaknesses by crawling into the application. Netsparker can depict and propose help methodology for shortcomings found. Also, security answers for forefront weakness evaluation are open.

- OpenVAS
OpenVAS is an astonishing weakness evaluation filtering instrument that maintains huge degree checks which are fitting for associations. You can use this gadget for finding shortcomings not just in the web application or web servers, but also in operating systems, data sets, organizations, and virtual machines.
OpenVAS gets updated day by day, which broadens the weakness identifying inclusion. It furthermore helps in hazard evaluation and suggests countermeasures for the shortcomings identified.

- W3AF
W3AF is a free and open-source device known as Web Application Attack and Framework. This apparatus is an open-source weakness evaluation instrument for web applications. It makes a design which helps with getting the web application by finding and exploiting the shortcomings. This instrument is known for usability. Along weakness filtering options, it has abuse offices utilized for entrance testing fill in also.
Also, W3AF covers a high-wide assortment of weaknesses. Organizations that are attacked often, particularly with recently discovered weaknesses, can choose this instrument.

- Arachni
Arachni is also a devoted vulnerability device for web applications. This device covers an assortment of weaknesses and is refreshed routinely.
Arachni is a free and open-source weakness apparatus that upholds Linux, Windows, and macOS. Additionally, Arachni aids entrance testing by its capacity to adapt up to recently recognized weaknesses.

Summary
Security dangers are continually developing. As a security proficient, you should have the option to distinguish the risks of new dangers. One approach to distinguish new dangers is to perform standard vulnerability assessments. A vulnerability assessment is the way to find new weaknesses in your system.
When a new weakness is found, it’s often called a zero-day attack. It is the type that is dispatched immediately after discovering vulnerability.
FAQ
References
Subscribe for the latest news