What is FIDO (Fast Identity Online)?
The era of passwords is going to end. They are ineffective in keeping the data protected from the current generation of hackers, which is way too advanced and smart. Cybercriminals of the present day know almost every trick to decode a password. Even if you have a strong password, you can’t sit back and relax. So, what’s going to protect the data then?
Welcome FIDO. A highly advanced security approach, FIDO is the new kid on the block that is making high waves because of its outstanding security strategy. Let’s find out more about FIDO meaning and its process.

FIDO - Introduction and Purpose of Existence
Let’s start with the basic FIDO meaning.
FIDO stands for Fast Identity Online and is an upcoming data and API security approach. It’s an open-source and standard security strategy emphasizing the use of public-key cryptography for credibility-verification in place of passwords, which seems inefficient for protecting organizational data.
Managed by FIDO Alliance, the FIDO protocol combines public-key cryptography and multifactor authentication to create a highly robust data and API security verification system that isn’t easy to bypass.
In recent times, we witnessed very severe cyber-attacks. Many of these even happened when a highly strong password was in place. But, only a password was used. No other security measures were adopted. This made industry experts wonder whether having a strong password is enough from a security point of view.
Well, the truth is, a password is no longer capable of protecting sensitive data. Have a look at a few statistics to understand this.
- On average, one internet user has nearly 90 online accounts, which makes password management tough.
- Nearly 50% of passwords are reused, which is no less than a threat for cybercriminals as simply guessing one password will have them unlock multiple accounts.
Out of all the data breaches happening today, 80% are happening because of poor passwords.
FIDO Alliance aims to make people and organizations understand that they are not safe with a password alone. Hence, FIDO came into being. This strong website and application security protocol combine MFA and public key cryptography that is practically unbreakable.
What makes FIDO way ahead of passwords is its information storage process. Passwords are saved on a website or application server, which makes them more prone to attacks and breaches.
But, FIDO stores identity-check related details or personal information on the user’s device only. This way, the user has full control over the login and identity-verification data. As it comes with API integration, it’s easy to generate multiple FIDO login credentials for different devices and hardware.
Both U2F and UAF are supported by this process of authenticating users, which adds up to its efficacy. UAF integration permits end-users to generate entirely new FIDO security key pairs at the time of registration.
The user will have access to the private key, while the public key will be with the website/application user is trying to use. When the user will access the website/application, authenticity-check of the private key will take place in the form of PIN, fingerprints, voice confirmation, or selfie upload.
The use of the U2F protocol allows FIDO to use a robust second factor for authenticity-checking. This 2nd factor could be a USB security token, or a device within 4.5 cm (via Near Field Communication). Login is only possible when the user injects or touches the U2F devices.
The history of the FIDO
FIDO adoption may have accelerated in recent times, but the FIDO Alliance has existed for a very long time. It was 2007 when PayPal started looking for an advanced MFA for its services. Even though login with OTP was introduced, very few people showed interest in this. Hence, further research started.
Ramesh Kesanupalli, who was the CTO of Validity Sensors at the time, presented the idea of fingerprint scanning into PayPal services. The then-CISO of PayPal, Michael Barrett, liked the idea and emphasized on the introduction of an industry standard that can mentor website/application authentication hardware approaches.
Kesanupalli started working on it. His efforts paid off well in 2013 when FIDO Alliance came into being. Slowly, the group grew, and some top players in the IT industry like Google, Master Card, ARM, Dell, Microsoft Corporation, Samsung, and many more became a part of it.
FIDO and How it Proceeds with Authentication
Now that you’re aware of the FIDO meaning and the history of the FIDO Alliance, it’s time to understand how this identity-verification method works.
If you’re trying to access a website that uses FIDO authentication, this is how registration or login will go:
- You forward an account creation request.
- The FIDO service provider will ask for the public key from the user.
- You need to complete the process using any of the WebAuthn-supported methods. You can take the help of the same device or another device that supports CTAP to complete the procedure.
- Once this stage passes, the device you’re using will create a cryptographic key pair that includes a private and a public key. The former will be linked to your device and data, while latter will be handed over to the FIDO service provider that further stores it to link it with your new account.
- Upon creating a new account, you have to take the same identity-verification route that involves:
- Sending login requests from the device
- Receiving a digital signature from the service provider and using it verify your identity.
- The device will connect the unique identity-verifying details while the service provider will generate the digital signature using the private key.
- The service provider will take the help of a public key to decode the signature and confirm it.
.jpg)
UAF (Universal Authentication Framework) - Introduction and Working
Content for Picture:
- User Registration begins
- The user will be redirected to pick his preferred authentication method.
- A key pair is created (specific to the Device + Service)
- Upon success, keys are exchanged. The user device keeps the private key; the service provider gets the public one.
- Registration completes.

UAF is used by FIDO for digital device user authentication. It’s applicable only on tablets, smartphones, PCs, and laptops. In case a user wants to access a website/application that deploys UAF standard, s/he has to register the account first with the help of the device. The device will prompt users to use supportive user identity verification methods.
After that, the user device will generate a new key pair that is device and service-specific. Upon successful initiation of the identity-checking process, the end-user device and service provider will only exchange cryptographic keys.
The same authentication techniques will be used each time a user accesses the linked account. The private key remains with the end-user while the public key is shared with the service provider.
The attention-worthy feature of UAF is that the service provider remains ignorant of the authentication data used. But, the technique of authenticating users used is known. Also, they are allowed to choose which auth type to accept and which to reject. This grants great flexibility to the services provider.
Also, the entire communication remains utterly encrypted and secured as biometric details and private keys remain saved on the user's device. Hence, the odds of security breaches are very less.
U2F (Universal Second Factor) - Introduction and Working
Content for Picture:
- User visits the sign-in page.
- Enter email/username and password details.
- Requires completing a security challenge that requires accessing a registered device.
- Device responds by completing the challenge and signing it with its key.
- Online service gets the signed challenge and verifies the key
- Upon successful verification, the user can now access the account or use the service.

We already provided a gist of U2F at the beginning of the post. Let’s learn more about it as it plays a crucial role in FIDO authentication. U2F stands for Universal Second Factor, and the protocol urges end-users to introduce a second factor at the time of login. It involves using a hardware device as 2nd login factor.
After the password is provided, users have to access that second factor, which could be a USB security token or NFC. The role of the second factor here is to store the private security key and provide it as and when required.
It was developed by Google as a result of its anti-phishing strategy. After successful internal usage, it was offered to FIDO Alliance. What’s worth noting here is that U2F doesn’t eliminate passwords completely. But, it makes use of simple passwords safe. When combined with a 4-digit PIN password, U2F can provide substantial security.
As far as its operations are concerned, a specific cryptographic key is exchanged with the service provider so that 2FA is done. Fob must be offered after multiple authentication attempts. Fob deploys the private key to ensure the authenticity of the website. This way, it prevents cyber threats like phishing and MITMA. Like UAF, U2F is also end-to-end encrypted and highly secured.
FIDO2 - Introduction and How it differs from FIDO?
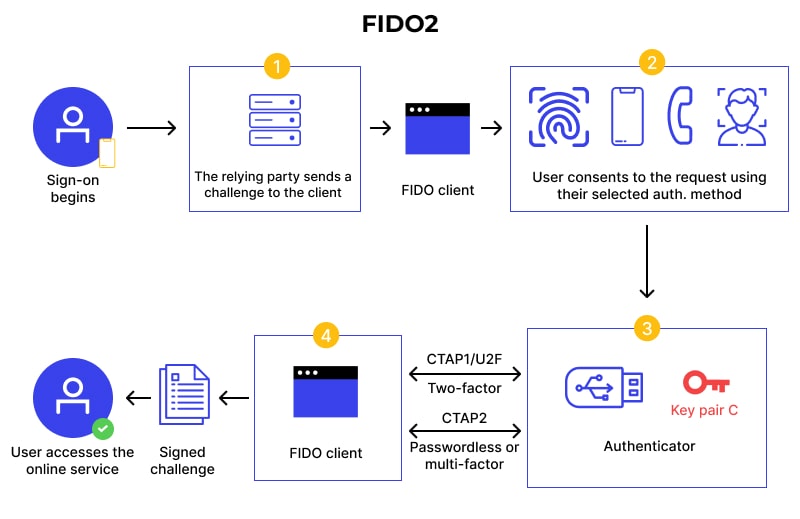
Content for Picture:
- User visits the sign-in page.
- The relying party/service shares a challenge with the FIDO client
- The user allows it to proceed and use its preferred auth method
- The FIDO client fetches a private key from the authenticator.
- As per the method (CTAP1/U2F and/or CTAP2), it signs the challenge.
- Online service gets the signed challenge and verifies the key
- Upon successful verification, the user can now access the account or use the service.
Just like any other security approach, FIDO also goes through changes and upgrades to remain relevant. The latest version, FIDO 2, is advanced and claims to fix the primary yet prominent FIDO glitches. Yes, there are flaws in FIDO. Even if it’s far better than its contemporaries, it’s not perfect. The concerning loopholes of FIDO are
The inability of UAF to work on PCs. It can only work on mobile.
Mandatory requirement to own and carry another device to use U2F. Even if the device/gadget is small, FIDO U2F users are forced to carry it everywhere they go.
These two shortcomings of FIDO forced FIDO Alliance to proffer an improved version. Hence, FIDO came into being. It’s based on FIDO and works towards promoting the practice of going passwordless, more secure, and easy to implement. Like FIDO, FIDO 2 also has two standards that support each other.
The first aspect of FIDO 2 is WebAuthn. It came into being in 2019 at the hands of W3C and promotes the usage of the public key for authentication. It’s like FIDO only. But, it’s not only mobile-device compatible.
Any data-driven device or PC – using JavaScript API-based browser – is compatible with WebAuthn. Practically speaking, all the devices meet this requirement. Hence, you can use FIDO 2 on almost every device.
The second specification of FIDO 2 is CTAP or Client to Authenticator Protocols. The role of CTAP is to permit any WebAuthn service provider to be seamlessly paired with the end user's PC and allow the use of a distinct authentication device. The specification is further divided into two categories, CTAP 1 and CTAP 2.
On a structural level, CTAP 1 is updated or refurbished U2F. Hence, it’s possible to use U2F key fobs with a WebAuth device so that 2FA is easily implemented.
CTAP2 is the extended form of its version 1. It permits data-driven devices, wearables, and smartphones to pair seamlessly with a PC to promote password-free login. The pairing generally takes place using a Wi-Fi connection, USB, or Bluetooth.
If you need a crisp comparison between FIDO and FIDO 2, have a look at the below-mentioned table.
FIDO Alliance is keeping an eye on the industry trends and improving the authentication procedure accordingly.
FIDO Certification
Considering the efficacy and effectiveness of FIDO, many organizations are trying to be FIDO certified. If you’re a company offering software or a device, being FIDO certified will pay off well, as the certification will help your audience to know that you’re a security-conscious business and are creating safe products. The best part is that FIDO specs are freely available, and anyone can use them.
Android became FIDO certified in 2019, while Safari earned this credibility much later. In 2020, Safari will become FIDO certified.
Presently, all the leading browsers are FIDO certified. Becoming FIDO certified is not an effort and a time-consuming job. There is a whole list of resources that will help you to become a FIDO-compliant business. Understand that there are different compliance procedures for hardware and interoperability. Play wise and adhere with the relevant procedure for both these aspects.
FAQ
References
Subscribe for the latest news