Exploit in Cyber Security
In the 21st century, we have seen the appearance of an assortment of innovative frameworks and cycles. Be that as it may, digital dangers have likewise become more perilous. Presently, attackers can search for various ways of separating and gaining passage into your framework. One of these ways is using an exploit. In this piece, we'll find out the significance and sorts of exploit. Let's begin!

Exploit Definition
An exploit or weakness is a piece of programming, information, or succession of orders that exploits a weakness to cause accidental conduct or to acquire unapproved admittance to delicate details. Whenever these weaknesses are recognized, they are posted on Common Vulnerabilities and Exposures (CVE). CVE is a free exploit word reference intended to work on worldwide network protection and digital flexibility by making a normalized identifier for a given weakness or openness.
Contrast Between Exploits And Vulnerabilities
Vulnerabilities versus exploit — what's the distinction? As referenced, vulnerabilities or gaps will be shortcomings or security blemishes in a framework or organization that can permit malevolent entertainers or programmers a way in. So, on the off chance that a vulnerability is an open window into the framework, an exploit is the rope or stepping stool the criminal uses to arrive at the open window. An exploit endeavor is an apparatus made to use a particular gap — without gaps, there's nothing to take advantage of.
That doesn't imply that every gap can be handily taken advantage of. Once in a while, the idea of a specific vulnerability is with the end goal that programmers can't sort out some way to compose code that exploits it. Getting back to our open window similarity, not all open windows provide food impeccably to attackers — at times, they're excessively high up to reach, or they may lead just to a locked cellar. This remains constant with "open windows" that are security defects — cybercriminals can't generally exploit each window.
In addition, vulnerabilities can be risky all alone, as they can cause framework crashes or glitches. A gap may welcome DoS (refusal of administration) or DDoS (appropriated forswearing of administration) assaults, in which assailants can cut down a site or basic framework without utilizing an adventure. Gaps exist in numerous sorts of programming, and individuals can likewise accidentally open up more shortcomings all alone — for instance, by using helpless security settings on their web-based media or email accounts. (That is the reason it's critical to realize how to change your protection settings on Facebook and make your Instagram account private.) Security imperfections can likewise be found in equipment, like the malignant Meltdown and Specter CPU weaknesses.
How Do Exploit Attacks Work?
Exploits take advantage of a security imperfection in a working framework, piece of programming, PC framework, Internet of Things (IoT) gadget, or other security weakness. When a weakness has been utilized, it frequently becomes known to the product engineers of the weak framework or programming and is regularly fixed through a fix and becomes unusable. This is why numerous cybercriminals, just as military or government organizations, don't distribute exploits to CVE but decide to keep them hidden. When this occurs, the weakness is known as a zero-day weakness or zero-day exploit.
One renowned illustration of an administration organization (the NSA) deciding to keep a product weakness hidden is EternalBlue. EternalBlue took advantage of inheritance variants of the Microsoft Windows working framework that utilized an obsolete adaptation of the Server Message Block (SMB) convention. Cybercriminals additionally fostered the WannaCry ransomware worm that took advantage of EternalBlue, and it spread to an expected 200,000+ PCs across 150 nations with damages going from many millions to billions of dollars before EternalBlue was fixed. Despite programming engineers giving a fix to EternalBlue, this realized weakness is a huge network safety hazard due to client reception of the hole.
Petya and its amusingly named replacement, NotPetya, were ransomware strains (NotPetya additionally depended on the EternalBlue exploit). The Petyas caused enormous harm by scrambling PCs' lord record table (MFT), delivering the machines unusable. And keeping in mind that there were permission requests made, NotPetya couldn't be unscrambled. So regardless of whether the clients and associations settled up, they got nothing consequently.
Specialists gauge that Petya strains of ransomware caused more than $10 billion in harm as they blew through banks and different organizations. BlueKeep is also an exploitable weakness in Microsoft Remote Desktop Protocol (RDP) that can permit aggressors to sign in to a casualty's PC from a distance. Microsoft raised the caution about BlueKeep in May 2019 and gave a fix in any event for obsolete working frameworks like Windows XP.
That uncommon advance shows the expected seriousness of BlueKeep: as it's another wormable exploit, numerous security analysts expected that BlueKeep would prompt the following crushing overall cyberattacks. As of this composition, BlueKeep presently can't seem to add up to much. However, it's imperative to fix your framework so you will not be trapped in any future assaults.

Since you've taken in the general working rule of exploit, it's an ideal opportunity to recognize the particular working system of specific exploits.
Remote weaknesses: This disturbs an organization and utilizes the fault without earlier admittance to the weak framework.
Nearby exploits: This requires earlier admittance to the weak framework and expands the advantage of the assailant past those allowed by the security manager.
Customer exploits: These are weaknesses against existing customer applications and normally comprise altered servers that send exploits when gotten to with a customer application. They may likewise require communication from the client and depend on friendly designing methods like phishing or lance phishing to spread or adware.
As a rule, these weaknesses are intended to harm the privacy, uprightness, or accessibility (CIA group of three) of programming or a framework. Numerous cybercriminals do this by focusing on various assault vectors, first acquiring restricted admittance then, at that point, utilizing a subsequent weakness to heighten advantages until they gain root access. That is why the people entrusted with ensuring data security, network security, and information security should utilize protection inside and out.
For instance, an aggressor could harm the secrecy of a PC by introducing malware on the PC, the uprightness of a website page by infusing malicious code into the internet browser, or accessibility by playing out an appropriated forswearing of administration (DDoS) assault fueled by a botnet of trojans.
Types of Exploits
There are two principal classes of exploits found in the present digital local area. They are known as known weaknesses and zero-day weaknesses.
Known weaknesses: These take advantage of safety scientists know about and have archived. It utilizes the target's realized weaknesses and is regularly fixed yet stays a suitable danger due to slow fixing.
Zero-day Exploits: These are weaknesses people have accounted for in the general population or recorded on CVE. This implies cybercriminals have observed the exploits before engineers have had the option to fix them, and some designers may not know about the weakness.

Different Exploit Categories
Exploits can be grouped into five general classifications:
- Hardware: This elaborates poor encryption, absence of board design, or firmware weakness.
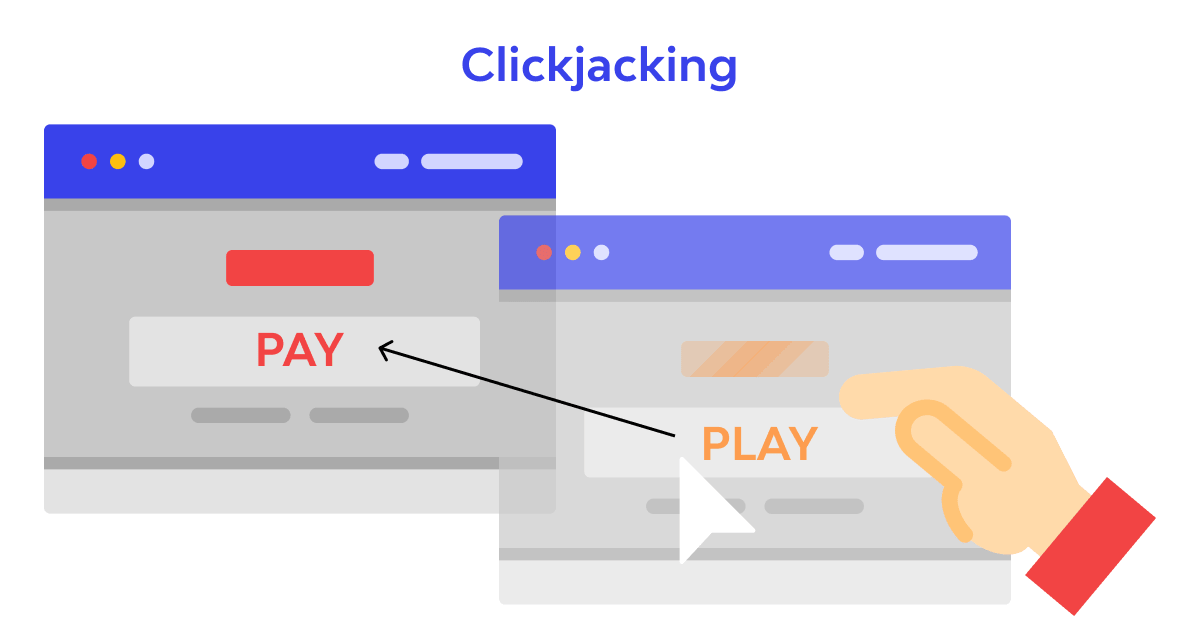
- Software: These dangers incorporate memory security infringement (support floods, over-peruses, hanging pointers), input approval blunders (code infusion, cross-site scripting (XSS), index crossing, email infusion, design string assaults, HTTP header infusion, HTTP reaction parting, SQL infusion), advantage disarray bugs (clickjacking, cross-site demand falsification, FTP ricochet assault), race conditions (symlink races, season of-check-to-season of-utilization bugs), side-channel assaults, timing assaults and UI disappointments (accusing the person in question, race conditions, cautioning weariness).
- Network: They incorporate decoded correspondence lines, man-in-the-center assaults, area capturing, typosquatting, helpless organization security, absence of verification or default passwords.
- Personnel: They incorporate poor enrolling strategy and interaction, absence of safety mindfulness preparing, helpless adherence to data security strategy, helpless secret word the board or succumbing to normal social engineering assaults like phishing, skewer phishing, pretexting, honey catching, smishing (smishing definition), water-holding, or whaling.
- Physical site: They incorporate poor actual security, closely following, and absence of keycard access control.
How Do I Detect An Exploit?
Since it utilizes security openings in programming, there aren't any ordinary signs you can perceive — a client has practically no chance of realizing they've been impacted until it's past the point of no return. That is why it's essential to consistently refresh your product and introduce security patches delivered by your product's designer. On the off chance that the engineer has provided a fix for a known weakness and you don't teach it, you'll leave the window open for programmers and other pernicious entertainers.
And keeping in mind that you probably won't see any weaknesses, once malware sneaks in, you're certain to feel the impacts. Search for normal indications of malware contamination, for example:
- Slow execution
- Continuous crashes or freezes
- Unexplained changed settings
- Huge loads of pop-ups or promotions where they shouldn't be
- Loss of extra storage
Assuming that you see any of these warnings, you ought to play out an infection filter with a trustworthy antivirus instrument immediately.
What is an Exploit Kit or Pack?
An Exploit kit or pack is a program that aggressors can use to dispatch exploits of known weaknesses in normally introduced programming like Adobe Flash, Java, and Microsoft Silverlight. A regular exploit kit gives an administration console, weaknesses designated at various applications, and a few modules that make it more straightforward to dispatch a digital assault.
Because of their robotized nature, exploit packs are a well-known strategy for spreading various malware and producing benefits. Makers of exploits bags might offer their adventure unit as help or an oddball buy. It is the most effective method to shield yourself from exploit attacks.
Your organization can alleviate the danger of exploits by introducing all product fixes when delivered, giving network protection mindfulness and OPSEC planning, and putting resources into security programming like an antivirus, automated leaked credential discovery, and data exposure recognition. It likewise pays to comprehend cloud security, as S3 security is defective by the plan.
The other regularly ignored assault vector that addresses critical network safety hazards are outsider merchants. Your sellers who process delicate information (for example, ensured wellbeing data (PHI), actually recognizable data (PII), or biometric information) can be the objectives of corporate surveillance or digital assaults, assuming they have more terrible network safety than your association.

How To Protect Yourself From Exploits?
Exploit risk management is an undeniably significant part of data hazard management. It involves putting resources into fostering a great third-party danger to the board structure, vendor management strategy, and digital protection hazard appraisal process. Ask current and likely sellers for their SOC 2 confirmation report and keep away from merchants who don't fulfill your security guidelines.
Third-party danger and fourth-party hazard are at the core of numerous information breaks and information spills. With the expense of information breaks, including third parties arriving at $4.29 million, it pays to forestall information breaks. On the off chance that your security group is little, consider automated vendor management policies. To put it plainly, center around forestalling exploits rather than tidying them up. Regardless of whether you remember you have been assaulted, IP attribution and automated legal sciences will not generally have the option to give you replies.
FAQ
References
Exploit - GitHub topic
How NotPetya has Insurers grappling with Systemic Cyber Risk - securityledger.com
Subscribe for the latest news











.jpg)