What is a web shell attack? How to detect and prevent it?
Introduction
Monthly web shell assaults have multiplied somewhat recently, as indicated by Microsoft. Your frameworks are at high risk of double-dealing in the event that you haven't conveyed guard procedures against this digital danger. Want to learn more on what a web shell attack is or how to find a web shell file? Continue reading.

What is a web shell?
Noxious contents known as web shells permit danger entertainers to commandeer web servers and execute extra attacks. Subsequent to invading a framework or organization, danger entertainers send a web shell. They use it as a long-lasting indirect access into the designated online applications and any related frameworks from here on out.
A distant aggressor can utilize a web shell to perform pernicious orders and take information on the off chance that it is effectively embedded into a web server. The Gallium bunch and the Lazarus bunch are two programmer bunches that have utilized web shells in their assaults.
Ways web shell works
- Relentless Remote Access
Secondary passages in web shell scripts permit assailants to remotely get to an uncovered server. For each malevolent activity, constant assailants don't have to take advantage of another weakness. A few assailants even fix the blemish they exploit to keep others from taking advantage of it and departure revelation.
To guarantee that main specific aggressors can get to them, a few internet based shells utilize measures like secret phrase verification. Web shells are regularly jumbled, including coding that keeps web indexes from boycotting the area where they are introduced.
- Acceleration of Privileges
Clients with restricted freedoms are oftentimes used to run web shells. By taking advantage of framework weaknesses to get root honors, aggressors can heighten honors by means of web shells. Assailants with root account access can do for all intents and purposes anything: introduce programming, adjust consents, add or eliminate clients, read messages, take passwords, etc.
- Assault Pivoting and Launching
Web shells can be utilized by assailants to turn to extra targets both inside and outside the organization. List (sniffing network traffic to find live has, firewalls, or switches) can require weeks, and assailants will stay under the radar to forestall location.
- Crowding Bots
Servers can be associated with a botnet by means of web shells (an organization of frameworks constrained by the aggressor). Aggressors utilize an order and control server associated with the web shell to send orders to the weak frameworks.
This is a typical DDoS assault strategy that requires a ton of data transfer capacity. Aggressors aren't straightforwardly going after the framework where the web shell is introduced; all things being equal, they're redirecting its assets to more positive targets.

Use of web shells by hackers
The employment of a web shell requires the assailant to initially recognize a framework weakness by means of which a web shell can be conveyed. They are habitually introduced by exploiting the server's or server setup's blemishes. This could include the accompanying:
- Application, record framework, and administration weaknesses.
- Remote document incorporation (RFI) and neighborhood record consideration (LFI) weaknesses (LFI).
- Execution of code from a good ways
- Organization interfaces that have been unveiled.
After effectively introducing a web shell, the aggressor can utilize it to run scripts on the objective host from a distance, permitting him admittance to touchy information put away on the association's servers.
Types of web shells
Let us take a look at the web shell file types there are:
- Bind Shell
A kind of shell that is placed on the objective gadget is Bind Shell. It is bound to a particular port on the host and screens the gadget for approaching associations. The programmer can then use this web shell to run scripts on the objective host from a far distance.
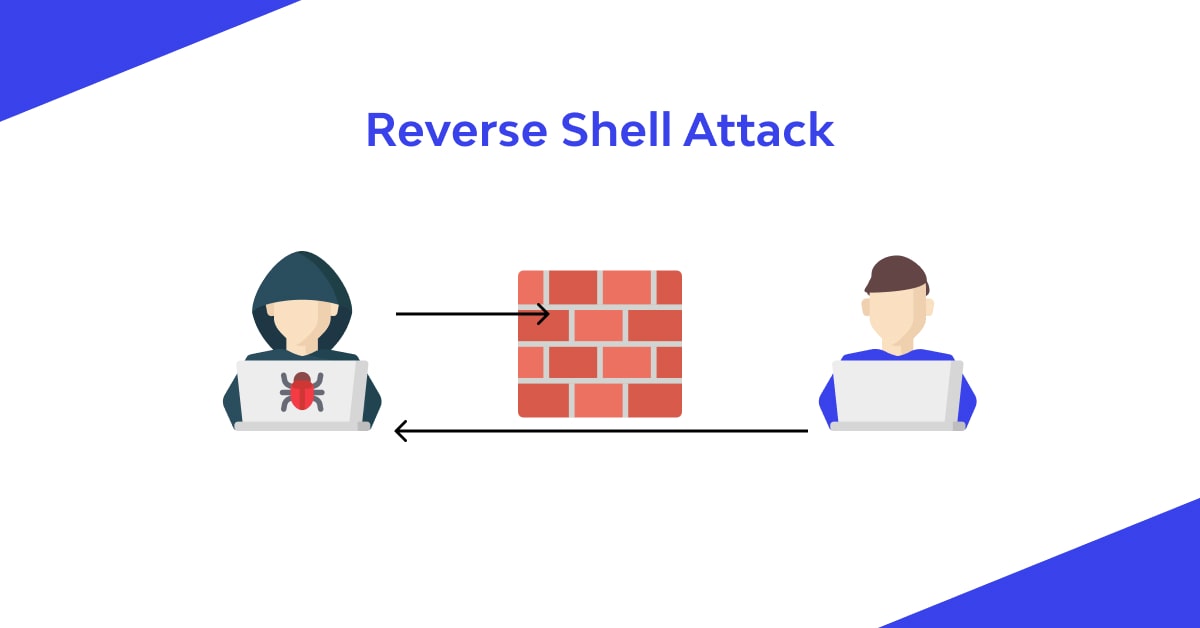
- Reverse Shell
An 'Associate Back Shell' is one more name for an opposite shell. For the conveyance of the web shell, the programmers should look for a remote order execution weakness and take advantage of it. The objective host associates back to the programmer's gadget, which tunes in for an approaching association, not at all like tie shell.
- Double Reverse Shell
A particular instance of the opposite shell is the twofold converse shell. The programmer's gadget, which was at that point tuning in for an approaching association, interfaces with the objective host. In any case, there are two ports that interface back to the programmer's gadget in the present circumstance. Both the information and result traffic are parted into two channels.

How to detect a web shell?
Coming up next are things to search for whether a framework executive speculates the presence of a web shell or is simply playing out a typical check.
To start, web shells should check the server access and issue logs for consistently utilized watchwords. The names of documents or potentially boundaries are incorporated here. The model underneath discloses how to look through the Apache HTTP Server's entrance log for the string record.
Look for extremely lengthy strings, which might demonstrate encoding. A few indirect accesses have great many lines of code.
Search for documents that have been altered during the last X days. In the accompanying model, we searched for *.php web shell documents that had changed the other day, yet every record modification ought to be examined on the grounds that a web shell could be implanted in a picture or another record.
Watch out for the organization for any surprising associations or traffic.
Look at the.htaccess records for any changes. Coming up next are a few cases of.htaccess document alterations that an assailant could make.
# The AddType mandate ties the chose content sort to the given filename expansions.
How to prevent and mitigate web shell attacks
- Implement the WAF
By separating all organization traffic, a Web Application Firewall (WAF) is intended to forestall web shells and hazardous payloads from being infused into a climate.
It's basic to keep up with your firewall in the know regarding the freshest network safety patches, similar as your antivirus programming.
- File Integrity Monitoring
Catalog refreshes are looked at against the timestamps of clean index scripts by a record trustworthiness observing help. On the off chance that a difference is found, the mentioned establishment on the designated web server's code registry will either be denied or a security cautioning will be set off.
- Checking the server configuration
By doing a careful server arrangement check, you can find and fix weaknesses in both the application server and the working framework.
- Network segmentation
By isolating organization fragments, you can keep programmers from accessing the whole organization by means of parallel crossing.
- Change the names of confidential directories
The registries that grant such transfers ought to preferably be completely deactivated to forestall the transfer of tainted picture records.
If such a transfer component is required, the delicate indexes' default names ought to be changed to make them more challenging to track down. To safeguard against insider dangers, just advantaged clients ought to approach these changes.
Also, make a channel for the document types that are permitted to be transferred to your web server.
- EDR
Web shell assaults can be relieved with the utilization of endpoint detection and response (EDR) and have logging frameworks. To distinguish web shells, these frameworks examine framework calls and cycle ancestry abnormalities, as well as utilizing examples of vindictive way of behaving.
- Reduce the number of plugins
WordPress modules are alluring assault vectors since anybody, including cybercriminals, can make them.
Just introduce modules from solid engineers and uninstall any that aren't expected to guard these vectors.
Protecting against attacks on the web shell with Wallarm
Wallarm's industry-driving Web Application Firewall safeguards against online shells and different dangers that speak with C&C servers, forestalling attacks with elite examination of web traffic to your applications.
Wallarm offers full security for applications, APIs, and microservices, including: FAST, API Security Platform, Advanced Bot Protection, DDoS Protection, Attack Analytics, and Client-Side Protection, notwithstanding the WAF.
FAQ
References
Subscribe for the latest news